Performing Incident Response and Forensic Analysis
Section 1: Hands-On Demonstration
Part 1: Analyze a PCAP File for Forensic Evidence
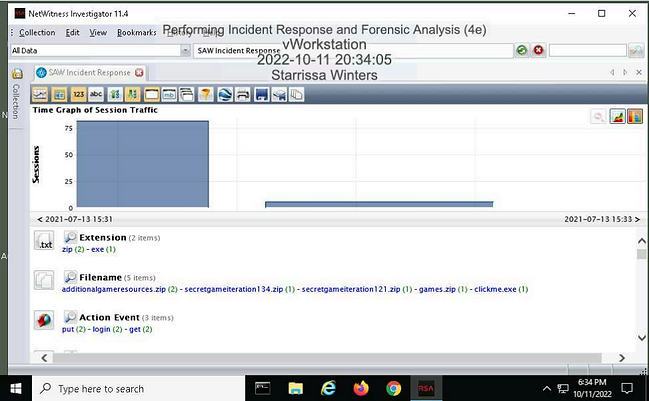
Make a screen capture showing the Time Graph.
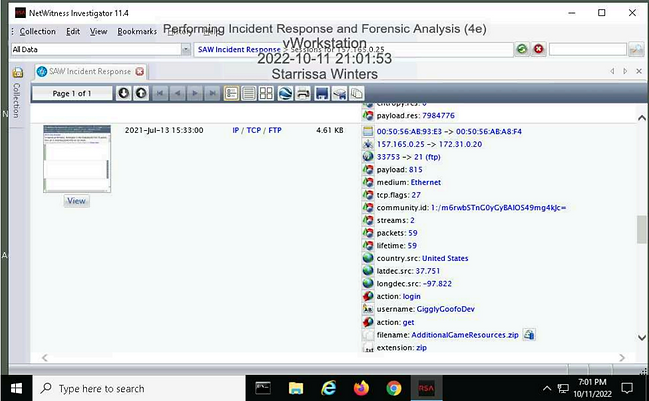
Make a screen capture showing the details of the 2021-Jul-13 15:33:00 session.
Part 2: Analyze a Disk Image for Forensic Evidence
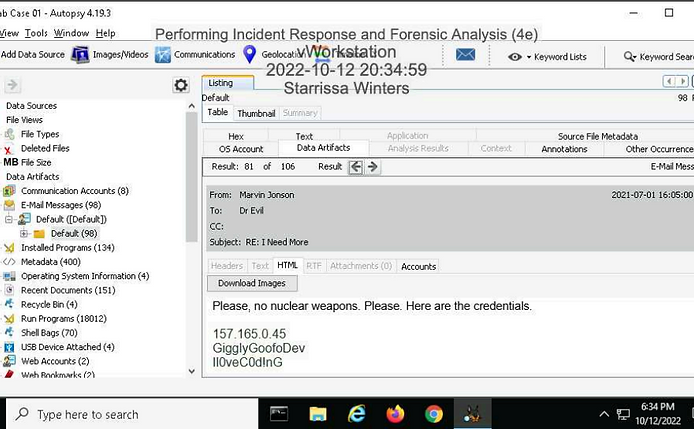
Make a screen capture showing the email message containing FTP credentials and the associated timestamps.
Section 2: Applied Learning
Part 1: Identify Additional Email Evidence
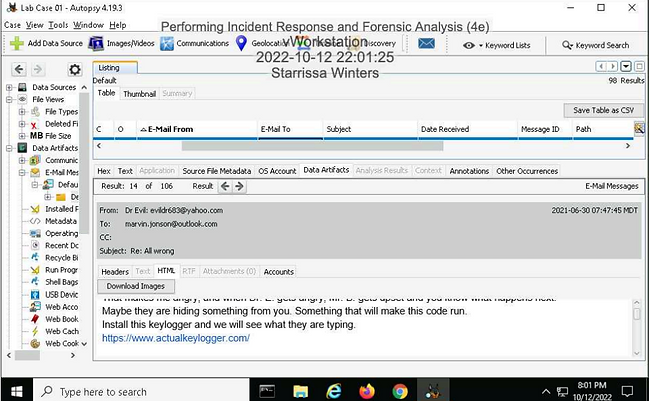
Make a screen capture showing the email from Dr. Evil demanding that Marvin install a keylogger
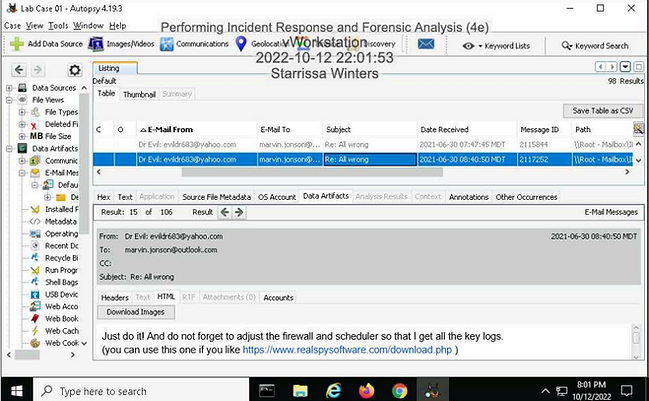
Make a screen capture showing the email from Dr. Evil reminding Marvin to update the firewall and scheduler.
Part 2: Identify Evidence of Spyware
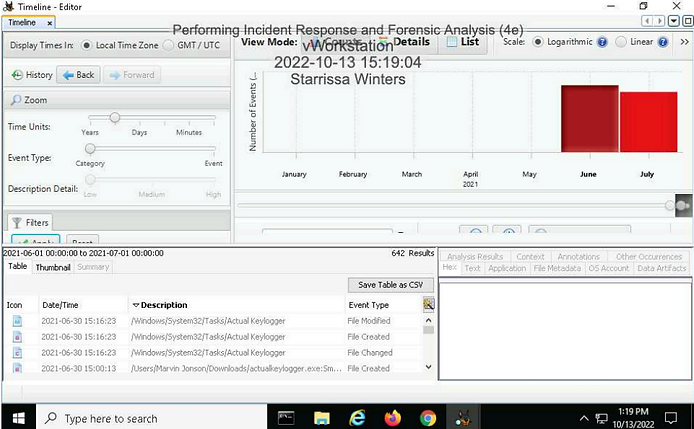
. Make a screen capture showing the three events that are related to the Actual Keylogger file in the /Windows/System32/Tasks folder with a June 30 timestamp.
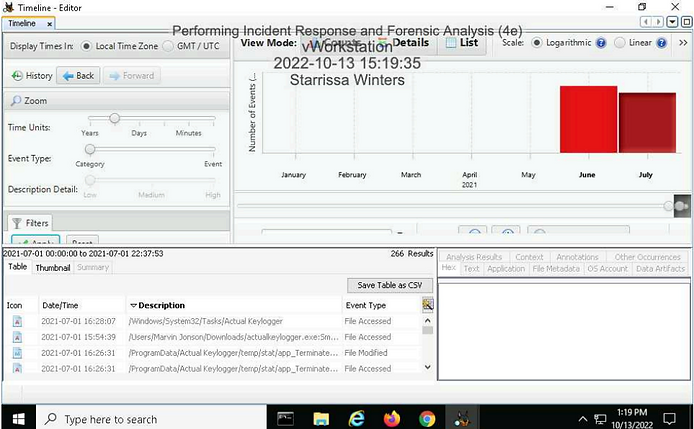
Make a screen capture showing the one event that is related to the Actual Keylogger file in the /Windows/System32/Tasks folder with a July 1 timestamp.
Section 3: Challenge and Analysis
Part 1: Identify Additional Evidence of Data Exfiltration
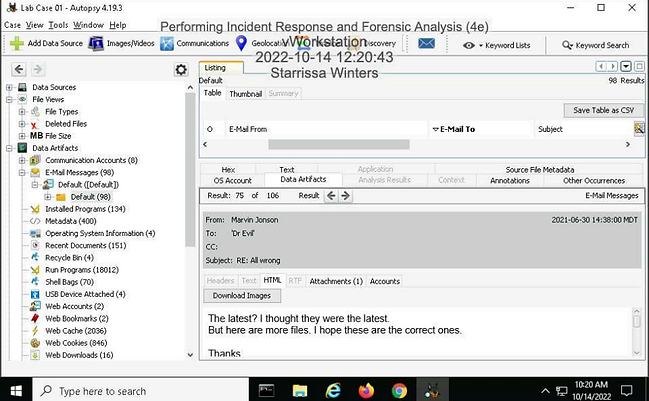
Make a screen capture showing an exfiltrated file in Marvin's Outlook database.
Part 2: Identify Additional Evidence of Spyware
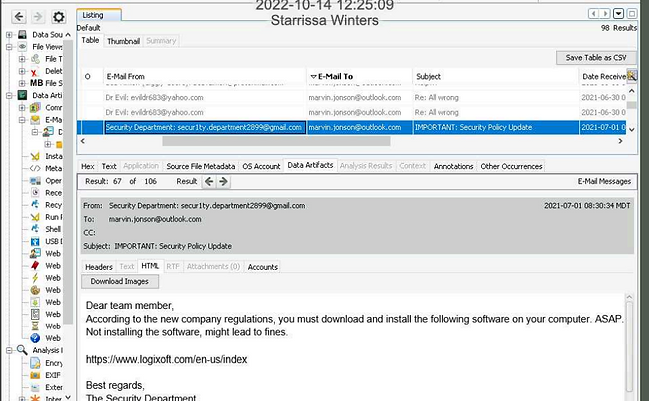
Make a screen capture showing the email with instructions for installing additional spyware.
Document the red flags in the email that indicate that it may be a phishing attempt. The red flags are grammar and spelling is unprofessional. The tone of the email is very casual/friendly and tries to appeal to Marvin's humanity. The sender uses slang and abbreviations that are not befitting in the environment.